第一个直接反编译就能看到
第二个
local_2c = 'F';
local_2b = 0x4c;
local_2a = 0x41;
local_29 = 0x47;
local_28 = 0x7b;
local_27 = 0x53;
local_26 = 0x54;
local_25 = 0x41;
local_24 = 0x43;
local_23 = 0x4b;
local_22 = 0x2d;
local_21 = 0x53;
local_20 = 0x54;
local_1f = 0x52;
local_1e = 0x49;
local_1d = 0x4e;
local_1c = 0x47;
local_1b = 0x53;
local_1a = 0x2d;
local_19 = 0x41;
local_18 = 0x52;
local_17 = 0x45;
local_16 = 0x2d;
local_15 = 0x42;
local_14 = 0x45;
local_13 = 0x53;
local_12 = 0x54;
local_11 = 0x2d;
local_10 = 0x53;
local_f = 0x54;
local_e = 0x52;
local_d = 0x49;
local_c = 0x4e;
local_b = 0x47;
local_a = 0x53;
local_9 = 0x7d;
local_8 = md5_hash(&local_2c);
|
丢给gpt
第三个
void entry(void)
{
CHAR local_4a4;
undefined local_4a3 [1027];
char *local_a0;
MD5 local_9c [144];
HRSRC local_c;
undefined4 local_8;
MD5::MD5(local_9c);
local_4a4 = '\0';
memset(local_4a3,0,0x3ff);
local_8 = 0;
local_c = FindResourceA((HMODULE)0x0,"rc.rc",(LPCSTR)0x6);
local_8 = 0x110;
LoadStringA((HINSTANCE)0x0,0x110,&local_4a4,0x3ff);
local_a0 = MD5::digestString(local_9c,&local_4a4);
MessageBoxA((HWND)0x0,local_a0,"We\'ve been compromised!",0x30);
ExitProcess(0);
}
|
有点麻烦,数据从0x110读取的,也就是272
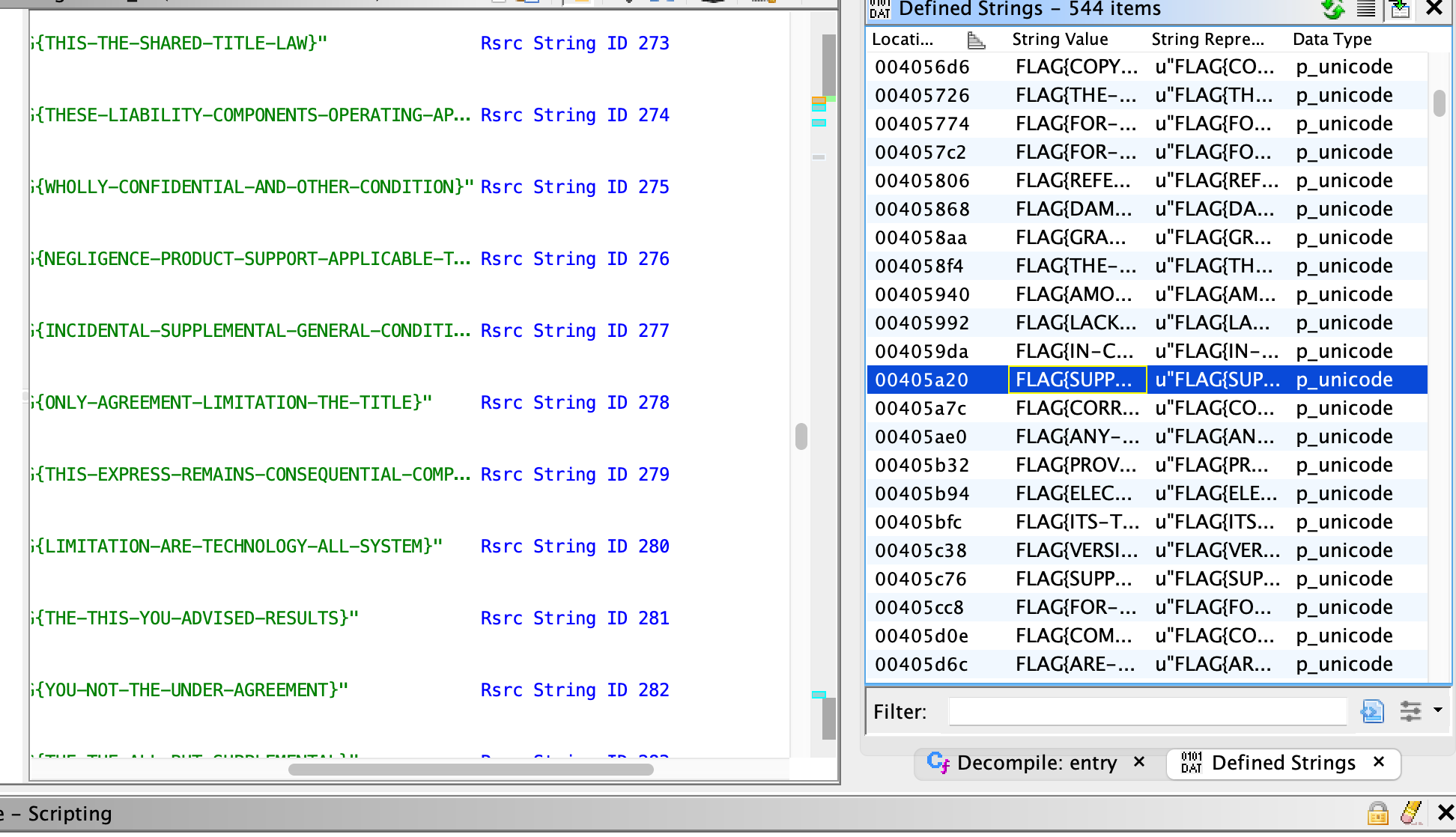
windows define的strings找到对应id

